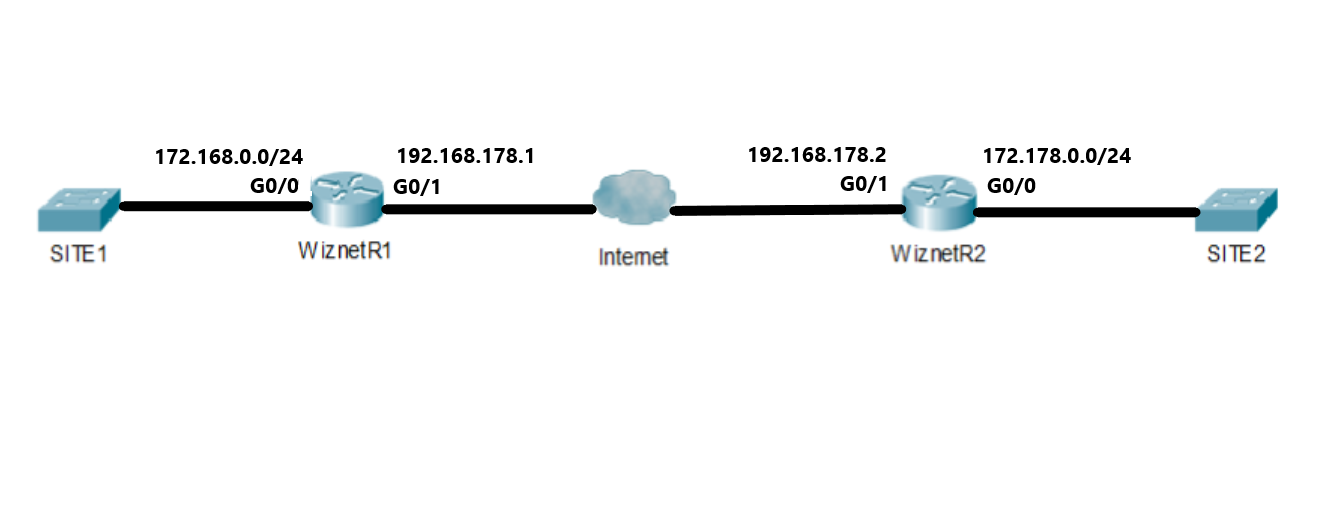
In this lesson we will see how to configure configure Site-to-Site IKEv2 IPSec VPN . In order to implement the VPN among the Sites, we have to follow the steps below:
1.Configure Host name and Domain name in IPSec peer Routers
2.Define IKEv2 Keyring
3.Define IKEv2 Proposal
4.Define IKEv2 Policies
5.Define Crypto ACL to identify the IPSec secured traffic
6.Define the Transform Sets
7.Define IKEv2 Profiles
8.Define Crypto Maps
9.Activate Crypto Map
Step 1: Configure Host name and Domain name in IPSec peer Routers
Configure the hostname on R1:
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname WiznetR1
WiznetR1(config)#exit
WiznetR1#
Configure the Domain name on WiznetR1:
WiznetR1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
WiznetR1(config)#ip domain-name Wiznet.com
WiznetR1(config)#exit
WiznetR1#
Configure the hostname on R2:
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname WiznetR2
WiznetR2(config)#exit
WiznetR2#
Configure the Domain name on WiznetR2:
WiznetR2#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
WiznetR2(config)#ip domain-name Wiznet.com
WiznetR2(config)#exit
WiznetR2#
Step 2: Define IKEv2 Keyring
Define IKEv2 Keyring in WiznetR1:
WiznetR1#configure terminal
WiznetR1(config)#crypto ikev2 keyring KEY1
WiznetR1(config-ikev2-keyring)#peer SITE2
WiznetR1(config-ikev2-keyring-peer)#address 192.168.178.2
WiznetR1(config-ikev2-keyring-peer)#pre-shared-key W1zn3tD0tC0m
WiznetR1(config-ikev2-keyring-peer)#exit
WiznetR1(config-ikev2-keyring)#exit
WiznetR1(config)#exit
WiznetR1#
Define IKEv2 Keyring in WiznetR2:
WiznetR2#configure terminal
WiznetR2(config)#crypto ikev2 keyring KEY2
WiznetR2(config-ikev2-keyring)#peer SITE1
WiznetR2(config-ikev2-keyring-peer)#address 192.168.178.1
WiznetR2(config-ikev2-keyring-peer)#pre-shared-key W1zn3tD0tC0m
WiznetR2(config-ikev2-keyring-peer)#exit
WiznetR2(config-ikev2-keyring)#exit
WiznetR2(config)#exit
WiznetR2#
Step 3: Define IKEv2 Proposal
Define a IKEv2 Proposal in WiznetR1:
WiznetR1#configure terminal
WiznetR1(config)#crypto ikev2 proposal PROPOSAL-SITE2
WiznetR1(config-ikev2-proposal)#encryption aes-cbc-256
WiznetR1(config-ikev2-proposal)#integrity sha512
WiznetR1(config-ikev2-proposal)#group 24
WiznetR1(config-ikev2-proposal)#exit
WiznetR1(config)#exit
WiznetR1#
Define a IKEv2 Proposal in WiznetR2:
WiznetR2#configure terminal
WiznetR2(config)#crypto ikev2 proposal PROPOSAL-SITE1
WiznetR2(config-ikev2-proposal)#encryption aes-cbc-256
WiznetR2(config-ikev2-proposal)#integrity sha512
WiznetR2(config-ikev2-proposal)#group 24
WiznetR2(config-ikev2-proposal)#exit
WiznetR2(config)#exit
WiznetR2#
Step 4: Define IKEv2 Policies
Define IKEv2 Policy in WiznetR1:
WiznetR1#configure terminal
WiznetR1(config)#crypto ikev2 policy POLICY-SITE2
WiznetR1(config-ikev2-policy)#proposal PROPOSAL-SITE2
WiznetR1(config-ikev2-policy)#exit
WiznetR1(config)#exit
WiznetR1#
Define IKEv2 Policy in WiznetR2:
WiznetR2#configure terminal
WiznetR2(config)#crypto ikev2 policy POLICY-SITE1
WiznetR2(config-ikev2-policy)#proposal PROPOSAL-SITE1
WiznetR2(config-ikev2-policy)#exit
WiznetR2(config)#exit
WiznetR2#
Step 5: Define Crypto ACL to identify the IPSec secured traffic
Configure a Crypto ACL in WiznetR1:
WiznetR1#configure terminal
WiznetR1(config)#ip access-list extended SITE1-SITE2-CRYPTO-ACL
WiznetR1(config-ext-nacl)#permit ip 172.168.0.0 0.0.0.255 172.178.0.0 0.0.0.255
WiznetR1(config-ext-nacl)#exit
WiznetR1(config)#exit
WiznetR1#
Configure a Crypto ACL in WiznetR2:
WiznetR2#configure terminal
WiznetR2(config)#ip access-list extended SITE2-SITE1-CRYPTO-ACL
WiznetR2(config-ext-nacl)#permit ip 172.178.0.0 0.0.0.255 172.168.0.0 0.0.0.255
WiznetR2(config-ext-nacl)#exit
WiznetR2(config)#exit
WiznetR2#
Step 6: Define the Transform Sets
Configure the Transform Set in WiznetR1:
WiznetR1#configure terminal
WiznetR1(config)#crypto ipsec transform-set SITE2-TRA-SET esp-aes esp-sha512-hmac
WiznetR1(cfg-crypto-trans)#exit
WiznetR1(config)#exit
WiznetR1#
Configure the Transform Set in WiznetR2:
WiznetR2#configure terminal
WiznetR2(config)#crypto ipsec transform-set SITE1-TRA-SET esp-aes esp-sha512-hmac
WiznetR2(cfg-crypto-trans)#exit
WiznetR2(config)#exit
WiznetR2#
Step 7: Define IKEv2 Profiles
Configure IKEv2 Profiles in WiznetR1:
WiznetR1#configure terminal
WiznetR1(config)#crypto ikev2 profile SITE2-IKEV2-PROFILE
WiznetR1(config-ikev2-profile)#match identity remote address 192.168.178.2 255.255.255.255
WiznetR1(config-ikev2-profile)#authentication local pre-share
WiznetR1(config-ikev2-profile)#authentication remote pre-share
WiznetR1(config-ikev2-profile)#keyring local KEY1
WiznetR1(config-ikev2-profile)#exit
WiznetR1(config)#exit
WiznetR1#
Configure IKEv2 Profiles in WiznetR2:
WiznetR2#configure terminal
WiznetR2(config)#crypto ikev2 profile SITE1-IKEV2-PROFILE
WiznetR2(config-ikev2-profile)#match identity remote address 192.168.178.1 255.255.255.255
WiznetR2(config-ikev2-profile)#authentication local pre-share
WiznetR2(config-ikev2-profile)#authentication remote pre-share
WiznetR2(config-ikev2-profile)#keyring local KEY2
WiznetR2(config-ikev2-profile)#exit
WiznetR2(config)#exit
WiznetR2#
Step 8: Define Crypto Maps
Define Crypto Map in WiznetR1:
WiznetR1#configure terminal
WiznetR1(config)#crypto map CRYPTO-MAP-SITE2 10 ipsec-isakmp
WiznetR1(config-crypto-map)#set peer 192.168.178.2
WiznetR1(config-crypto-map)#set pfs group24
WiznetR1(config-crypto-map)#set security-association lifetime seconds 3600
WiznetR1(config-crypto-map)#set transform-set SITE2-TRA-SET
WiznetR1(config-crypto-map)#set ikev2-profile SITE2-IKEV2-PROFILE
WiznetR1(config-crypto-map)#match address SITE1-SITE2-CRYPTO-ACL
WiznetR1(config)#exit
WiznetR1#
Define Crypto Map in WiznetR2:
WiznetR2#configure terminal
WiznetR2(config)#crypto map CRYPTO-MAP-SITE1 10 ipsec-isakmp
WiznetR2(config-crypto-map)#set peer 192.168.178.1
WiznetR2(config-crypto-map)#set pfs group24
WiznetR2(config-crypto-map)#set security-association lifetime seconds 3600
WiznetR2(config-crypto-map)#set transform-set SITE1-TRA-SET
WiznetR2(config-crypto-map)#set ikev2-profile SITE1-IKEV2-PROFILE
WiznetR2(config-crypto-map)#match address SITE2-SITE1-CRYPTO-ACL
WiznetR2(config-crypto-map)#exit
WiznetR2(config)#exit
WiznetR2#
Step 9: Activate Crypto Map
Apply Crypto Map to the WAN Interface on WiznetR1:
WiznetR1#configure terminal
WiznetR1(config)#interface gi0/1
WiznetR1(config-if)#crypto map CRYPTO-MAP-SITE2
WiznetR1(config-if)#exit
WiznetR1(config)#exit
WiznetR1#
Apply Crypto Map to the WAN Interface on WiznetR2:
WiznetR2#configure terminal
WiznetR2(config)#interface gi0/1
WiznetR2(config-if)#crypto map CRYPTO-MAP-SITE1
WiznetR2(config-if)#exit
WiznetR2(config)#exit
WiznetR2#